Facebook Applications Spreading Adware

A new scheme allows cyber-criminals to monetize on unwary users by leading them into installing adware applications. Rather than using hidden vulnerabilities in the social networking platform, this novel approach relies on social engineering in order to trick users into interacting with the attacker.
Step 1: The Application
The central element of the scheme is the Dance Class Video, application, a third-party extension of Facebook that has neither been developed, nor approved by the social network. The application’s page has been artificially populated with content and friends to increase the victim’s confidence. The application’s main purpose is to send specifically crafted messages and to continue recruiting new victims, as described below.
Step 2: The Bait
The infection vector is simple yet efficient. Compromised accounts send spammy messages that impersonate a Facebook video: “[victim’s name], this video is from the dance academy i went to last week.. what do u think?”. As soon as the victim follows the link, the application would ask for confirmation to pull out personal data, to send message on users’ behalf, as well as permission to always send these messages without any further confirmations.
Step 3: Request for permission to publish without your knowledge in the image below!
Step 4: Request to permanently allow the application is shown in the image below.
Step 5: The Payload
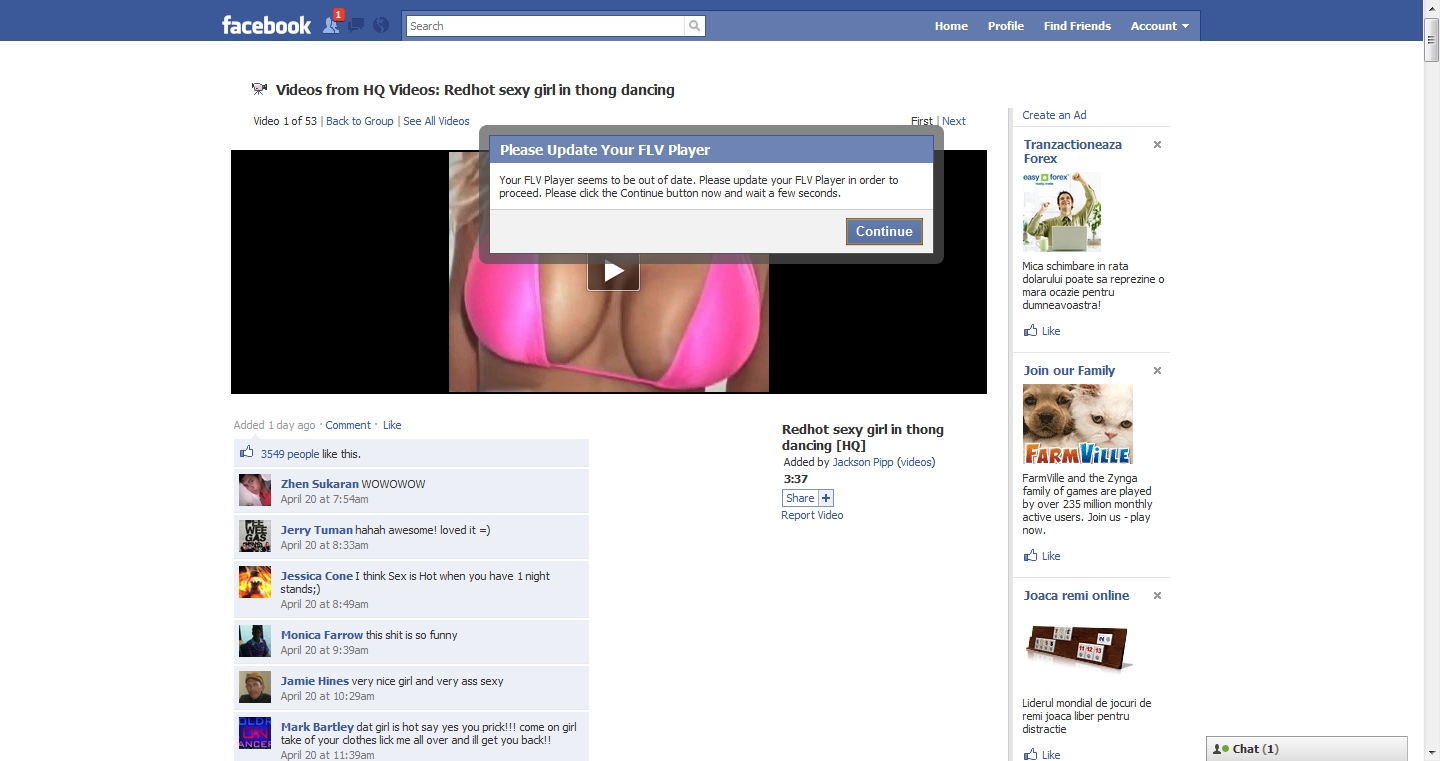
After all the necessary confirmations have been pulled from the victim, they would be redirected to the application’s page that displays a fake video player (which is in fact a JPEG image hosted outside of Facebook), prompting them to update their FLV player in order to be able to see the video. See image below.
The download page even contains an End-User License Agreement and the small provision that the SB 140 Alaska rule expressly forbids an application to engage in deceptive acts or practices described in this subsection using spyware by causing a pop-up advertisement to be shown on the computer screen of a user by means of a spyware program”. The page also triggers the automatic download of a binary file called FLVDirect.exe.
And Finally…
Once downloaded and installed, the binary file would hijack the browser’s start page and search settings without the user’s consent.
Apart from all the trouble a piece of adware may inflict to the average computer user, please remember that your social networking profile may hold sensitive information and granting third parties access to it or to act on your profile may have extremely dangerous repercussions on your privacy.
Read more at Malwarecity.com